Picture this scene in the not too distant future: An instrument technician at a busy industrial site obtains clearance to install a new process sensor. He mounts the sensor to the prepared tapping point and makes sure everything is tight. He obtains clearance from the control center to crack open the isolating valve and commission the new sensor. The two-way on his belt crackles, and the duty operator in the control-center confirms the new sensor reading has appeared at his DCS monitor.
The instrument tech packs away his wrench and heads in for a coffee. The installation took him less than an hour. The sensor used a new wireless technology known as Zigbee, self-powered by a small internal battery.
Zigbee is coming. Whether you intend to use wireless or not, by the end of this decade, most instrumentation and automation products will have embedded wireless as a standard feature. Zigbee, also known as wireless mesh, is a new open wireless standard for wireless sensors.
Wireless in the control and automation world is evolving quickly. What was simply a novelty a few years ago is now becoming an established technology in industry. Ignoring this new technology won't be an option; I&C practitioners will need to come to grips with wireless as they have for every other new technology.
Other markets using sensing and control, such as HVAC, building management, and security, are already going wireless. The change process has started, and wireless will dominate these markets. Industrial wireless will follow in the same way Ethernet migrated to the industrial environment, driven by its low price and dominance in the outside world. Zigbee was principally developed for the volume markets of HVAC, security, and home automation. At its heart is an embedded low RF power transceiver, powered from an integral lithium battery.
Low power is the key to Zigbee. Most importantly it keeps the RF design simple, which keeps the price down, probably the prime concern for the HVAC and security markets. Low RF power also means low battery consumption. Having to connect power wires to a wireless sensor defeats the purpose, so wireless sensors need to be battery powered, and low RF power means an acceptable battery life.
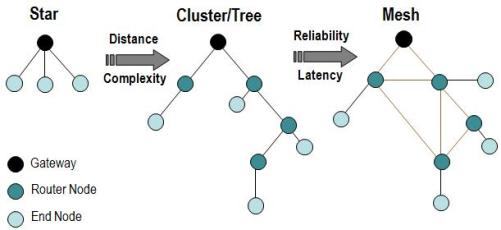
Unfortunately low RF power also means short wireless operating distance, but Zigbee gets around this problem by forming a mesh. Zigbee transceivers can talk to each other, passing on wireless messages. Each sensor or node only has to transmit as far as the next node. A group of Zigbee devices automatically form a mesh, with each wireless message routing via the optimum path. If one device fails, the mesh self-heals, re-routing messages via the next best path.
And with future Zigbee chips envisaged at around $20 each, you can see why Zigbee will revolutionize HVAC and security. Sensors in these industries are already low cost, but wiring is expensive. Wireless sensors in HVAC means a lot more thermostats giving better control and lower energy costs. Wireless sensors in security means a much higher level of monitoring for the same outlay.
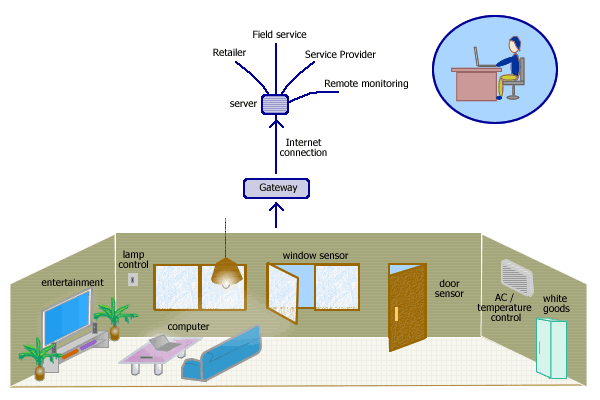
You probably wouldn't use an HVAC thermostat to monitor your hydro-cracker, and you won't need to. Zigbee can also fit into an industrial temperature transmitter as well as industrial flowmeters, level gauges, pressure transmitters, pH probes, and position sensors. In fact, it can fit all of the automation and process sensors we use every day.
But just because it is there doesn't mean you'll use it. We all know of products packed with high-tech features that don't see wide use. The same could happen with Zigbee. Industrial wireless products have been available for years, and there are concerns regarding latency delays and security. Wireless is not suitable for high-speed control applications, and this is unlikely to change. But it has proven reliable for most monitoring and slower control applications, that is, nearly 80% of automation and process applications. Technology has addressed security concerns, and to a large degree, has overcome them. The high cost of wiring has always been a constraint to collecting the nice-to-have plant data and turning it into useful information. Wireless can remove that constraint. But Zigbee has an added implicit weakness over traditional wireless because of its reliance on the mesh.
In the HVAC and security industry, customers will retrofit entire installations. Sensors are low-cost; it was the wiring that made installations expensive. It will be easy and inexpensive to cover buildings with HVAC and security sensors. A large wireless mesh will be easy to form. But industrial sensors are much more expensive. How many plants and factories are going to retrofit a large number of instrumentation sensors to form a mesh?
An added problem is RF propagation in an industrial environment will fade out long before a building environment. Steelwork is much harder to transmit through than drywall or masonry. Zigbee transmissions fade out in less than 100 feet in a lot of industrial applications. The reliance on the Zigbee mesh will be even greater.
Zigbee in the industrial environment will suffer from the eternal chicken-or-the-egg quandary. Which comes first, the sensor or the mesh? Without the mesh, Zigbee is limited. But without a large number of sensors, the mesh won't form. Early adopters will need to install a large number of Zigbee sensors before a mesh can form to transport the wireless signals.
The "Zigbee wireless sensor range in a typical plant" diagram is an example of an early adopter of Zigbee technology. Four wireless sensors have been installed, however none of them have the range to reach the control center, nor do they have the range to link to each other.
 |
A solution to this constraint is to integrate tomorrow's technology with today's. Existing wireless networks known as wireless information backbones (WIBs) use higher-power wireless to penetrate through the obstacles of modern plants. A WIB differs from Zigbee because it is not intended to embed into sensors but acts as a higher-level wireless network, transferring multiplexed information throughout a plant or factory.
A WIB is a wireless network of gateways, providing connectivity to a large number of different or similar data buses. As its name implies, it is a wireless backbone for sharing information. You could think of it as wireless protocol conversion, but this would be too simple an explanation. It is a peer-to-peer network that can handle multiple protocol conversions, interconnecting multiple fieldbuses, or databus LANs. And it's all done wirelessly.
 |
The advantage that the WIB has over Zigbee is power, RF power. Unlike Zigbee, which throttles its RF output to a few milliwatts, WIB nodes generate the full 1W of RF power allowed under FCC rules. A typical WIB node using 1W of RF power can penetrate through most plants and factories. A WIB has a similar mesh capability as Zigbee but rarely needs to use it. And a WIB solves the other problem facing Zigbee, the same problem hindering many data acquisition concepts, compatibility with the installed mass of existing fieldbuses and control room devices.
So why is Zigbee technology needed at all? The answer: cost. Because of its mass production and simple design, Zigbee devices will be a fraction of the cost of WIB devices. The wireless plant of the future will likely comprise two layers of wireless networks: Zigbee clusters for the sensor layer, and WIB networks for the controller layer.
 |
WIB nodes would include an embedded Zigbee transceiver. Information from the local Zigbee cluster would then be transmitted via the backbone to other WIB nodes, and transferred to physical devices via Ethernet, Profibus, DeviceNet, Modbus, and the like. Will the two wireless systems interfere? They certainly could if they used the same wireless bands. However, most Zigbee products are likely to use the 2.4GHz band, which already has low-cost components available from mass-produced wireless systems in the commercial market, Wifi and Bluetooth. And most WIB systems use the 900MHz band, which gives better transmission performance in industrial environments. So the two technologies can coexist without interference or congesting a single wireless band.